
Viruses, Adware, Spyware and Ransomware. Do you know how to protect your computer? – by Loc Nguyen
Let’s start with a brief history on Malware.
Everyone’s heard of the computer virus. It’s been around as long as computers have been. Over time and with the increase in availability of the internet different types of infections have cropped up exponentially. More recently the term Malware has been thrown around more. Malware or Malicious Software is a broad term used to describe all sorts of unwanted or malicious code of which the virus is one of them.
Zero Day Malware
This actually means that the Malware is so new that the companies that write the programs designed to protect you from Malware don’t even know about it yet. So how do you protect from something you don’t know exists? Chicken and Egg question…
In the years past virus’ tended to be either difficult to very difficult to remove and were designed to either steal information or just create havoc with your computer. Although they are difficult to remove, once removed though you can continue to use your computer as your data is still intact. With Ransomware they are generally nowhere near as difficult to remove but the damage has already been done. All those files listed above have been encrypted with an almost impossible to crack key. All there is to do now is to pay up. Your data is being held at ransom. Thus Ransomware.
Since these virus’ popped into main stream in 2013 they have made the hackers hundreds of millions of dollars worldwide. Now with experience and data to sift through they have realised that the ones that tended to pay are the small and medium business. So guess what? They know their target market!
These programs are written to target users in one of two ways. By exploiting holes in a web browser when you visit an unsafe website or via email. Either way in most business environments emails are the more likely ways to get hit. The emails look and feel very legitimate and are usually in the form of a electricity bill, or a resume but can be anything that a person will most likely open even letters from the Australian Federal Police! Sometimes the Malware isn’t in the email itself but will be hidden on a website that the email asks you to visit to say claim the parcel that Australia Post couldn’t deliver to you! Looks and sounds very legitimate no? Very clever.
There are different types of malware which can be grouped into the following categories:
- Virus
- Adware
- Spyware
- Worms
- Trojans
- Ransomware
So what are the differences?
Virus
A computer virus does what a virus does in people – it’s designed to replicate and spread and to whatever the designer intended it to do including sending back data to the designer or destroy data. It’s been around the longest and therefore everyone knows what an antivirus program is. These days’ viruses are actually not that common anymore but the name antivirus has stuck. Thank the marketing people.
Adware
Next time you watch a YouTube video, see those ads on the on the video or before them? That’s a form of adware or Advertising Supported Software. These are designed to generate revenue for the author. Not all adware is malicious though. Probably just more annoying.
Spyware
This does exactly that. It’s designed to spy on you. The most obvious form would be making a copy of every key you type. Some large companies actually use this on its staff PC’s.
Worms
This type of Malware is designed to have malicious intent. Generally designed to replicate and destroy information and data on your PC to the point of potentially rendering your PC in operable.
Trojans
These are based on the “Trojan Horse” theory. Designed to look and feel safe but silently in the background it’s stealing information and potentially rendering your PC inoperable.
Ransomware – this is the one we’re going to focus on as it’s new and improved and oh so very dangerous for small business.
It is basically an advanced piece of malicious software that once executed will scan and encrypt all your important data on your computer and any devices that is attached to it including mapped network drive letters until you pay the author for a key to decrypt all your data.
In earlier versions I limited itself to typical useful files. This is a list of the files that some of the earlier versions scanned for and encrypted.
*.xls *.doc *.pdf *.rtf *.psd *.dwg *.cdr *.cd *.mdb *.1cd *.dbf *.sqlite *.jpg *.zip
As you can see basically anything that is important to either yourself or your business.
You can get them from either visiting an infected website or via email.
The list below is the updated version of the files that the newer versions will scan for.

As you can clearly see there have been some major upgrades to the types of files that are scanned.
The problem is depending on the version you happen to get, it will encrypt some or all of the above files. Some will even take a copy of all your saved passwords in your browser and upload it to the hackers servers and to make it even worse the newest iteration of Ransomware will even rename all the encrypted files so you won’t even recognise your own files. This creates a new problem. How can you restore the file if you don’t know what the name of the file is?
3 short cases to show the difference in results after being hit with ransomware.
Case Study 1
Business / Holiday / Family Visit.
Mid 2014 I get a call from a friend who has a colleague who is visiting family on the Gold Coast but is also here to source products for their surf shop overseas. She does business on her laptop with everything in Excel spreadsheets. Unsure how she got infected but when I get there I see the familiar instructions on how to decrypt the files with a count down. The Malware is easy enough to remove but again the damage has been done. All files associated with her business that she had with her along with any USB drives that had been plugged in had been encrypted along with all her holiday photos. Basically gone. Unfortunately not much I could do for them.
Case Study 2
I get a call from front desk staff from a Health Clinic. The girl says “somethings wrong. When we open up a template to write notes all we see is random characters.” I get bad feeling. I log in to have a look and sure enough they’ve been hit with Cryptolocker (a version of ransomware). In this case they operate directly on the server so I can’t switch it off as they are still using it for the appointment book. I log in. Install Antivirus as all previous warnings to install one had gone unheard, do a scan and sure enough tens of thousands of files encrypted. I tell them the situation and tell them that I would need to restore all the data from backups. Silence. As you can probably tell that’s never a good sign. There were none as they had never needed one after years or practising.
One saving grace they had was the version of Ransomware they got hit with was one that didn’t encrypt databases. In this case the appointment book and images that had been inserted into the database was still intact. This allowed them to still see some notes, images and the appointment book. A couple of days later I called to check in and see how everything was going and was told by the front staff that “we were told to start recreating the templates and notes again from scratch”.
Case Study 3
A client who just so happen to be interviewing for an actual job opening in their business when they got an email with a resume. Bad timing. There was an attachment with a zip file of the so called resume. They opened it but couldn’t get the resume to open but as with most business were extremely busy and thought nothing of it, deleted the email and went on with their day. A few hours later they started to notice that their logo on letterhead wasn’t getting inserted when they tried to send out emails. The first call was to the software company for support. After some inspection they were told that all the settings were correct so there’s nothing the support people could do and that they should call their local IT person to have a look at the network. (this happens much more often than not). OK I thought sounds a bit strange so I log in remotely to have a look and everything looked right, and in that instance I hear a voice in the background saying and “oh I have been meaning to ask, on my computer I get this annoying popup saying that I need to pay for an encryption key”. Woops. I tell them to shut down all computers in the office starting with the server immediately and I will be out there in 30 mins. (luckily this particular client is physically close by).
First thing I do when I arrive on scene is unplug the network cable and switch on the server to run a full scan. You can see how many files it had encrypted in the image below. That was after I deleted a stack of them. Be sure to note the bottom of the screenshot. There’s 14 pages of this with each page showing 100 items. All up it had encrypted approximately 16000 (sixteen thousand) files consisting of PDF, JPG, DOCX, XLSX… you get the picture and it wasn’t even finished. It stopped when the server was shut down.
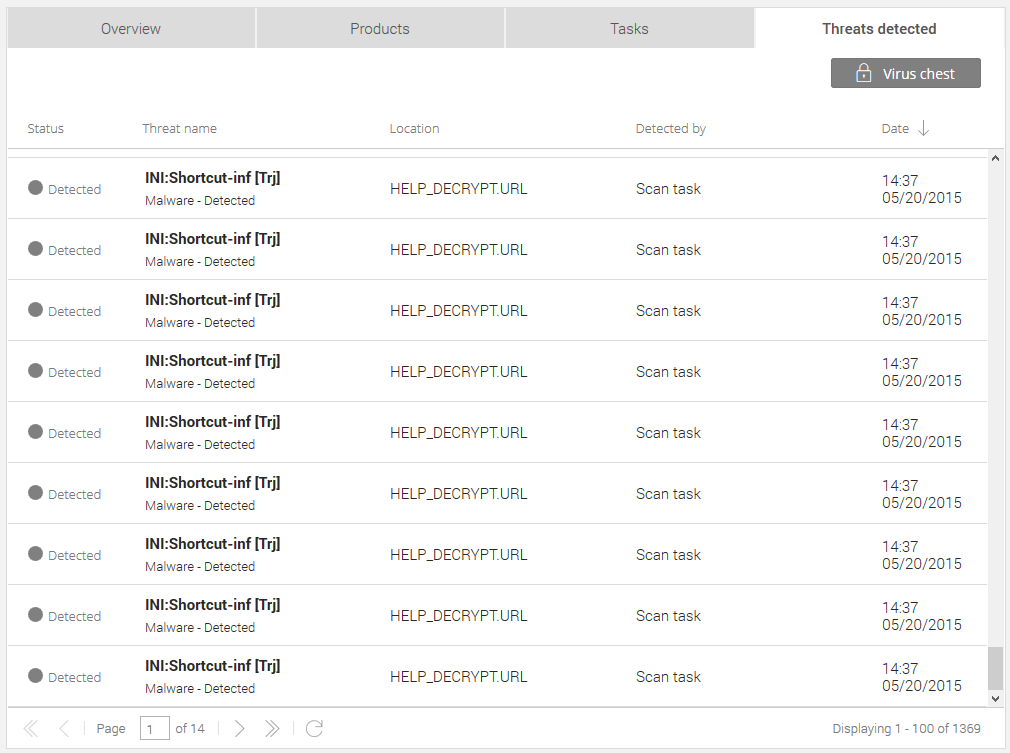
In this case the virus infected a particular workstation which had network mapped to the server. After it encrypted all the files on that particular workstation it started to encrypt the files on the server. The virus wasn’t even on the server! When I scanned the server it was clean of infection!
It was not all doom and gloom. They had one major thing work in their favour. They had in place a solid backup plan. In total they lost about half a day’s worth of data and for the rest of that day they took paper notes while the data was restored from backup.
Which scenario would you fall into?
Some things to look out for
Remember that these emails are not targeted specifically at one person or group in particular, instead it’s a scatter gun approach knowing the average person in a normal office environment gets hundreds of emails a day and that most people will just click on it to see if they should be checking it or deleting it.
So it just has to look legitimate for someone glancing at it or if you’re one of those clicks on everything, but when you actually look at the emails in detail it will become particularly obvious that it’s not legitimate.
Some basic rules of thumb to take notice of before opening any emails. Especially in a business environment where it can have devastating results.
- First and foremost look and see who the email is from? Do you recognise the sender? If you don’t recognise the senders name do you recognise the domain name? That’s the part of the email after the @ symbol which tells you what business they are from.
- If you don’t recognise the sender but the domain part is legitimate then look how they’ve addressed you in the email body itself. Really obvious spelling mistakes and or grammar is always a red flag as these emails are almost always written by people from non-English speaking backgrounds. In saying that I wouldn’t put it past locals to have bad grammar or the occasional spelling mistake, but look for really obvious errors. Also most legit emails will address you with your full name. I say most because I occasionally do get legitimate emails addressing me as dear sir, dear user, etc. and they have usually been from a budget internet provider or similar. It’s a shame that not all companies follow this rule but it’s a good place to start.
- If there is an attachment check to see what type of attachment it is. In nearly all cases, unless you recognise the sender. Never open up zip files or click on links in the email body.
What do these emails look like that so easily trick people into opening them up? Have a look for yourself. Do you think you’d be tempted to open them?
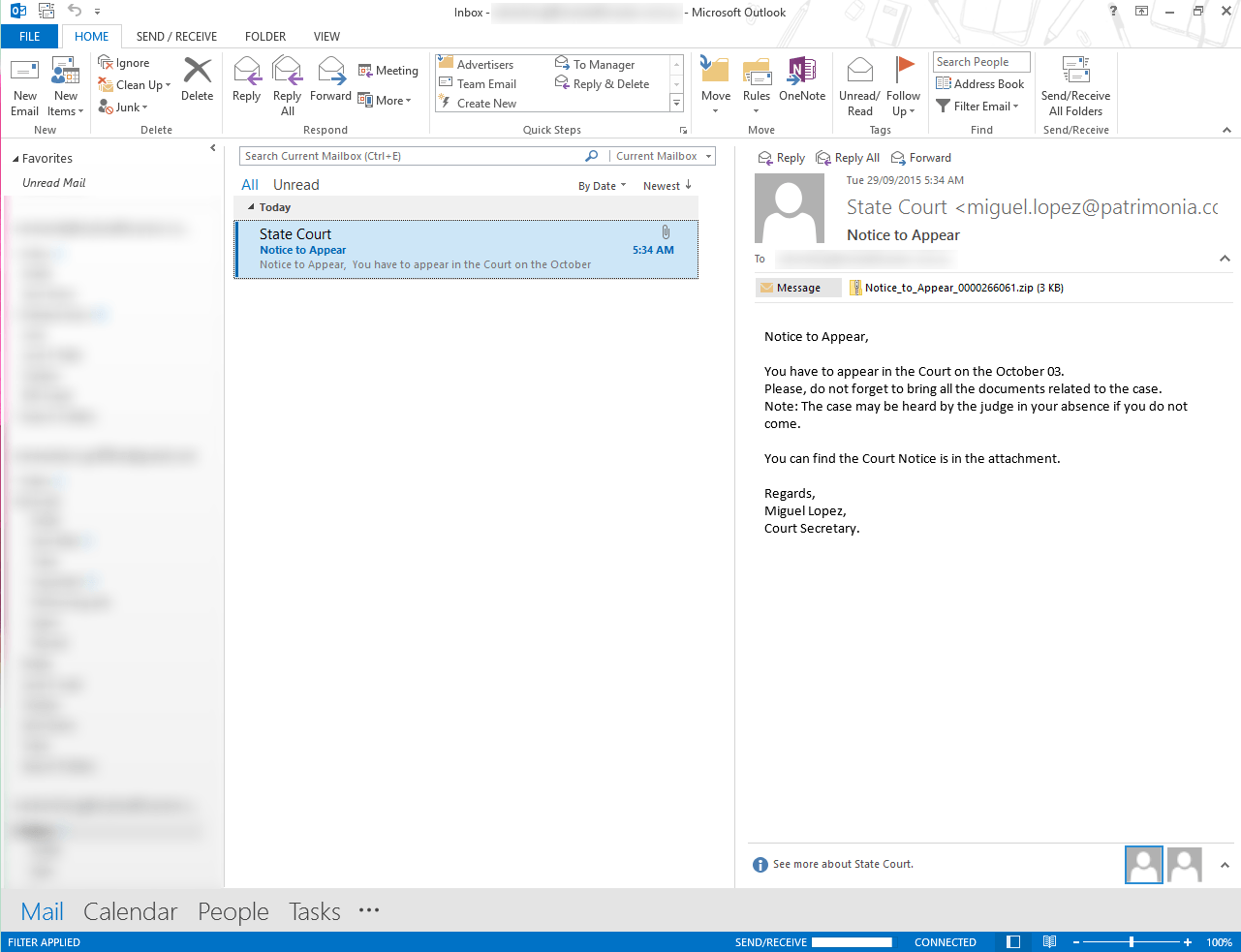
In this case what if you worked in a law firm? Could pass as legitimate if you’re busy and have tens of emails that are unread and need to be replied to yesterday.
If you look at it carefully some of the things discussed above can used to decide whether its legit or not are:
- Don’t recognise the sender especially the domain name (the part after the @ symbol) should raise red flags immediately
- It doesn’t address me by name
- If you read the message body carefully there are some basic grammar issues although this doesn’t necessarily rule it out but what does stand out is the date. It says October 03 but no year?
- There’s a zip file attached from an unknown sender. Lots of red flags!!!
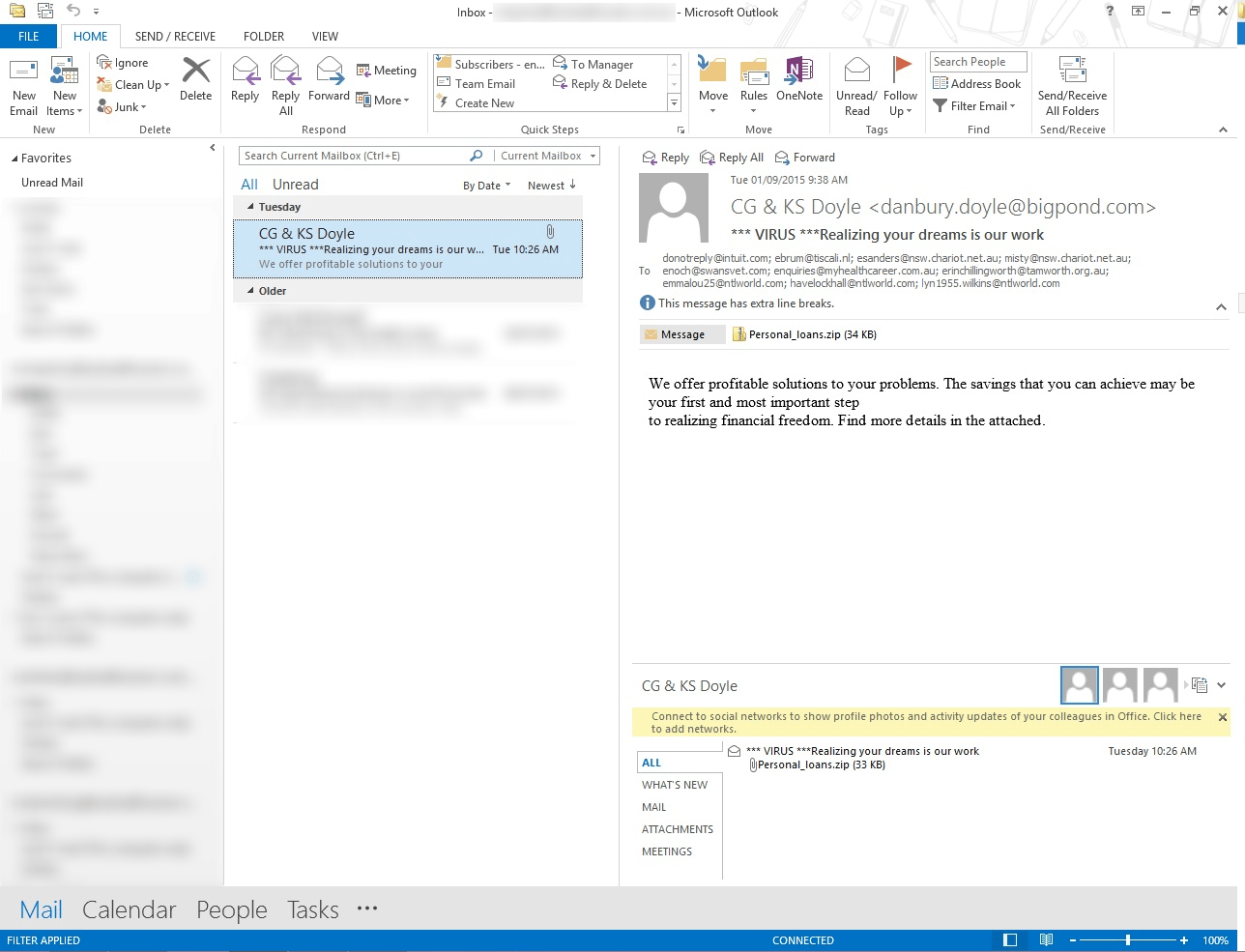
This one is a little different maybe more obvious to some but have a look at the senders details. In Australia that’s a very legit and common email address.
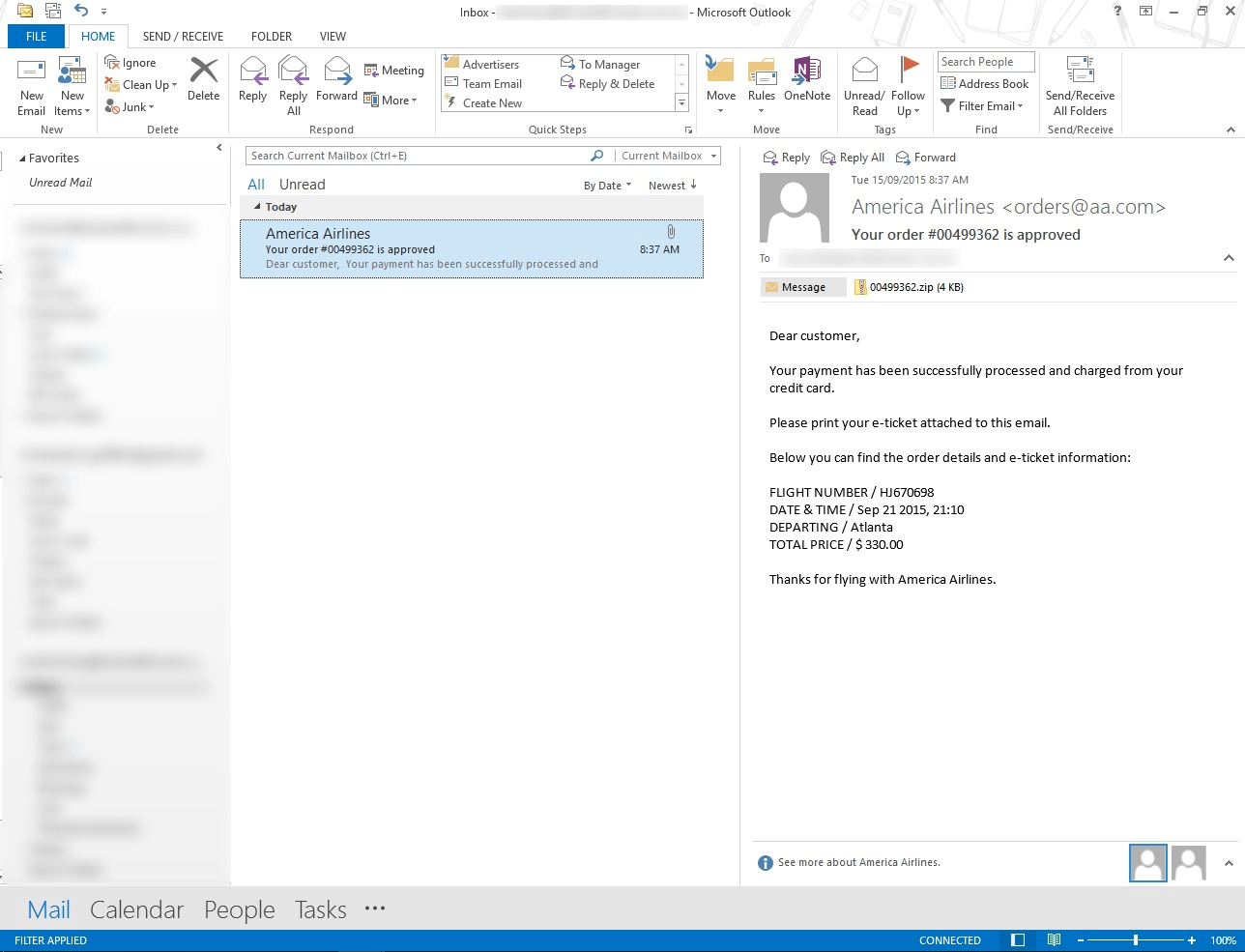
Being in Australia this one might be an obvious one to stay away from but what if you were in the U.S.A.? Or what if it was Qantas or Virgin? Again the senders email address looks like a legit and real email. It could also be pure co-incidence that you were actually travelling as well.
These are just a few that don’t necessarily relate to us here locally much but I have seen ones similar to the above which can be very easily mistaken such as in the above case study of resumes or even electricity or phone bills.
So how do you protect yourself from these attacks?
Like with so many things the best method of protection is first and foremost knowledge and also training. Anti-Virus programs will pick up some but the ones that get through will need human intervention and while it’s great that you yourself might be very protective of what gets through to you don’t forget your staff and make sure they are trained up in what to look for and what to delete.
Below are some suggestions. While there are never any guarantees these will at least help minimise the chances of your business getting infected.
- Make it a rule in your workplace to NEVER open any emails from people you don’t know. If it looks legitimate but you are unsure then pick up the phone and call to confirm or go directly to the website and never click on the links in the email if you don’t know the sender. Yes it’s time consuming but it’ll save you from potentially thousands of dollars in downtime.
- If you do get emails with attachments if it’s a zip file then delete immediately.
- Make sure your computers are up to date. Windows updates are annoying and frequent but they are released to plug the security holes that are found.
- Make sure you have antivirus and anti-malware programs and that they are up to date as well.
- Try not to click on ads, if you are actually interested call or go directly to the website
- Have good reliable backups. Yes with an “s” meaning more than one. Good rule of thumb is 3-2-1.
o At least 3 copies of the data
o 2 different mediums
o 1 kept remotely or offsite
- We’ll go into backups in much more detail in some upcoming articles so stay tuned it may save you literally thousands of dollars and potentially your business.
 Loc Nguyen is a lifelong technology geek whose aim in life is to deliver simple, workable IT solutions. Crusading during daylight hours to keep health practitioners up and running to allow them to do what they do best – looking after their patients, come sundown he protects their data by managing their backups with his proprietary LockDown system. Loc’s clients include medical practices, dentists, an orthodontist and an ophthalmologist. Go to www.locnguyen.com.au for more information about his services and to contact him for a technology solution tailored to your practice.
Loc Nguyen is a lifelong technology geek whose aim in life is to deliver simple, workable IT solutions. Crusading during daylight hours to keep health practitioners up and running to allow them to do what they do best – looking after their patients, come sundown he protects their data by managing their backups with his proprietary LockDown system. Loc’s clients include medical practices, dentists, an orthodontist and an ophthalmologist. Go to www.locnguyen.com.au for more information about his services and to contact him for a technology solution tailored to your practice.
More articles on My Health Career:
